Data Exfiltration Techniques Market Insights, 2031
The global data exfiltration techniques market was valued at $69.7 billion in 2021, and is projected to reach $217.5 billion by 2031, growing at a CAGR of 12.3% from 2022 to 2031.
Increase in online malware and misuse of the internet driving the data exfiltration techniques market growth. The malware infiltrate’s the data to an external server controlled by the outsider, who may then sell it or publish it. Hence, data exfiltration prevention and detection require an organization to have an adaptive security culture and solutions that utilize a spectrum of observables and indicators to assess the plausibility of various scenarios.
In addition, the surge in the incidents of data loss in the on-premise environment and the rise in sophisticated cyber threats for critical information theft. Thus, these factors drives the of the data exfiltration techniques market size growth. However, lack of standards and device compatibility issues and lack of skilled professionals in data exfiltration techniques market hampering the growth of the credit card issuance market size. On the contrary, surge in demand for cloud-based cyber security solutions will provide major lucrative opportunities for growth of the data exfiltration techniques market.
The movement of sensitive data from inside the organization to outside without authorization, is indicated by data exfiltration. This process can be carried out deliberately or accidentally through malware over a network. There are various techniques performed by cyber criminals for data exfiltration. It can be difficult to detect data exfiltration as the transfer or moving of data within and outside a company’s network is involved. Due to increase in the number of smartphone users, enterprises are adopting data exfiltration techniques for the protection of sensitive information. The data exfiltration techniques market is segmented into Type, Industry Vertical, Component and Enterprise Size.
Segment Review
The data exfiltration techniques market is segmented on the basis of component, enterprise size, type and industry vertical. By component, it is segmented into life solution and service. By enterprise size, it is bifurcated into larger enterprises and small & medium enterprise. By type, it is segmented into user activity monitoring, antivirus/anti-malware, firewall, intrusion detection system/ intrusion prevention system (IDS/IPS), encryption, data loss prevention and others. By industry vertical, it is segmented into BFSI, IT & telecom, retail & e-commerce, healthcare, manufacturing, government & defense, energy & utility and others. By region, it is analysed across North America, Europe, Asia-Pacific, and LAMEA.
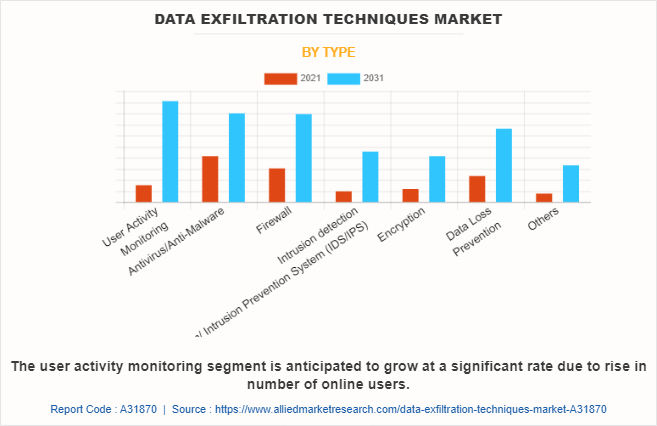
By type, the antivirus/anti-malware segment dominated growth of the data exfiltration techniques market in 2021, and is expected to maintain its dominance in the upcoming years, owing to rapid usage of antivirus and rise in number of cyber-attacks. However, the user activity monitoring segment is expected to witness highest growth during the forecast period, owing to rise in number of internet users.
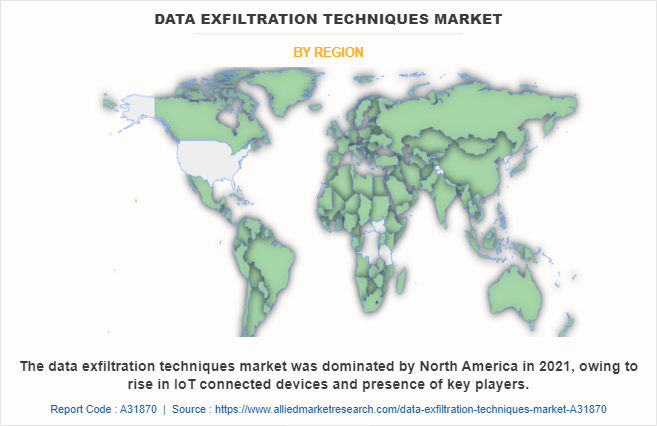
North America dominates the data exfiltration techniques industry in 2021. Growth of the market in this region is attributed to several factors such as increase in digitalization and adoption of data exfiltration techniques by the end users for added security. Moreover, presence of key players is providing ample growth opportunities for the market growth. However, Asia-Pacific is expected to witness highest growth rate during the forecast period, owing to rapid expansion of internet infrastructure across the region.
Top Impacting Factors -
Increase in online malware and misuse of the internet
Data exfiltration occurs when malware and/or a malicious actor carries out an unauthorized data transfer from a computer. It is also commonly called data extrusion or data exportation. Furthermore, it is also considered a form of data theft. Moreover, it can be conducted by outsiders, who penetrate the network in order to steal user credentials, intellectual property, and company secrets. In addition, outsider attacks usually start with the injection of malware onto an endpoint such as a computer or mobile device that is connected to the corporate network.
Further, the malware infiltrate’s the data to an external server controlled by the outsider, who may then sell it or publish it. Hence, data exfiltration prevention and detection require an organization to have an adaptive security culture and solutions that utilize a spectrum of observables and indicators to assess the plausibility of various scenarios. Therefore, these are the major growth factors for the data exfiltration techniques market.
The surge in the incidents of data loss in the on-premise environment
The shift to remote work over the past few months has increased the need for organizations to re-evaluate their security and risk management practices. With employees accessing corporate data at times on home computers or sharing and collaborating in new ways, organizations could be at greater risk for data leak or other risks.
For instance, to help companies with the visibility they need and better protect their data, in March 2020, HP Inc announced the launch of three new security solution that provides threat product for remote workforces as a countermeasure to support countries across the world experiencing lockdown due to COVID-19 pandemic. The solutions include HP Proactive Security, HP Sure Click Enterprise, and HP Pro Security Edition. These solutions allow users to run real-time protection with task-level isolation and non-persistent virtual machines avoiding data breach, and data exfiltration. Therefore, these are the major factors propelling the market growth.
The rise in sophisticated cyber threats for critical information theft
Data exfiltration occurs in various ways and through multiple attack methods, mostly on the internet or on a corporate network. The techniques cybercriminals use to extract data from organizations’ networks and systems are becoming increasingly sophisticated. These include anonymous connections to servers, Domain Name System (DNS) attacks, Hypertext Transfer Protocol (HTTP) tunneling, Direct Internet Protocol (IP) addresses, file less attacks, and remote code execution. Therefore, the rise in sophisticated cyber threats for critical information theft is the major driving factor for the data exfiltration techniques market.
Lack of standards and device compatibility issues
Data exfiltration is a malicious process where cybercriminals (such as external actors) or insiders (such as employees, contractors, and third-party suppliers) accidentally or deliberately steal or move data from inside to outside a company's perimeter without authorization. These scenarios occur when a user accesses information through an authorized channel and moves the data to an insecure local device.
For instance, someone can use cameras, computers, smartphones, or other specialized devices to capture data for exfiltration, either by downloading existing files from cloud services or copying the information into new files. Any files transferred to an insecure device are at high risk for data exfiltration. Therefore, these are the major factors limiting the growth of the data exfiltration techniques market.
Lack of skilled professionals
Organizations need to minimize the risk of human error that may result in data loss or theft. Since employees can make mistakes that attackers can leverage to their advantage. A user could unsuspectingly download an infected malware file, transmit their credentials through a phishing campaign, or otherwise neglect to secure their personal computer or other devices. Hence, it is essential to regularly train and educate employees on the latest security measures to avoid human error.
For instance, organizations should ensure that each person understands how to identify a suspicious email. Furthermore, the organizations should also make sure that employees know how to report a suspicious email so the security team can investigate and take any necessary action right away. To ensure appropriate security, organizations must educate their employees. Therefore, these are the major factors limiting the growth of the data exfiltration techniques market.
Surge in demand for cloud-based cyber security solutions
The integration of cloud-based solutions in data exfiltration techniques is expected to provide a major growth opportunity for the market. Business operations leveraging the cloud services expose businesses with new categories of data exfiltration risks, including instances where insecure access of cloud site features by the administrators, and employees would allow hackers to requisition virtual machines, deploy malicious code and thereby initiate outbound transmission of sensitive data.
For instance, in February 2020, McAfee announced the launch of global managed detection and response (MDR) platform and its strategic partnership with DXC Technology to leverage the MDR solution to proactively detect and resolve security incidents of its customers faster. The platform provides services including threat hunting, forensics and investigation, and complete managed endpoint threat detection and response. Therefore, these factors will provide major lucrative opportunities for the data exfiltration techniques market forecast.
Market Landscape and Trends
The growing need for security against increasing bot traffic, along with the rise in the number of smartphone users has led enterprises to adopt data exfiltration solutions for the protection of their sensitive information. Moreover, the small and medium-size enterprises (SMEs) are gaining a high traction in the market, as they are more targeted by internal and external data breaches. With the adoption of data exfiltration techniques, organizations can effectively maintain and secure their critical information from data breaches. Thus, data exfiltration techniques help organizations optimize employees' productivity, protect sensitive data, applications, and comply with stringent regulations.
In addition, technologies such as blockchain and artificial intelligence in data exfiltration techniques market is major growth factor. Furthermore, misuse of internet, online malwares, surge in the incidents of data loss in the on premise environment and growing refinement levels of data breaches are some of the major factors, contributing to the growth of data exfiltration techniques market share.
Key Benefits for Stakeholders
- This report provides a quantitative analysis of the market segments, current trends, estimations, and dynamics of the data exfiltration techniques market analysis from 2021 to 2031 to identify the prevailing data exfiltration techniques market opportunities.
- The market research is offered along with information related to key drivers, restraints, and opportunities.
- Porter's five forces analysis highlights the potency of buyers and suppliers to enable stakeholders make profit-oriented business decisions and strengthen their supplier-buyer network.
- In-depth analysis of the data exfiltration techniques industry segmentation assists to determine the prevailing market opportunities.
- Major countries in each region are mapped according to their revenue contribution to the global market.
- Market player positioning facilitates benchmarking and provides a clear understanding of the present position of the market players.
- The report includes the analysis of the regional as well as global data exfiltration techniques market trends, key players, market segments, application areas, and market growth strategies.
Data Exfiltration Techniques Market Report Highlights
| Aspects | Details |
| Market Size By 2031 | USD 217.5 billion |
| Growth Rate | CAGR of 12.3% |
| Forecast period | 2021 - 2031 |
| Report Pages | 292 |
| By Enterprise Size |
|
| By Type |
|
| By Industry Vertical |
|
| By Component |
|
| By Region |
|
| Key Market Players | Xorlab, Pen Test Partners, Exabeam, Tessian Limited, Juniper Networks, Inc., Fortra LLC, Barracuda Networks, Inc., Proofpoint, DTEX Systems Inc., Fortinet, Inc. |
Analyst Review
Due to increase in the number of smartphone users, enterprises are adopting data exfiltration solutions for the protection of sensitive information. Small and Medium-size enterprises (SMEs) are targeted by internal and external data breaches. The growing need for such security will drive the growth of data exfiltration techniques market. In addition, the movement of sensitive data from inside the organization to outside without authorization, is indicated by data exfiltration. This process can be carried out deliberately or accidentally through malware over a network. There are various techniques performed by cyber criminals for data exfiltration. It can be difficult to detect data exfiltration as the transfer or moving of data within and outside a company’s network is involved.
Furthermore, market players are adopting strategies for enhancing their services in the market and improving customer satisfaction. For instance, in October 2022, Proofpoint Inc., a leading cybersecurity and compliance company, announced integration with Microsoft Defender to provide organizations with advanced threat protection across email and endpoints. Proofpoint Targeted Attack Protection (TAP) will receive visibility on email threats via Microsoft Defender API. In addition, the integration adds unique new hashes to the customer’s Microsoft Defender custom intelligence. Once the Proofpoint IOC details are added to Microsoft Defender, an alert then be created by Microsoft Defender if related malicious content tries to execute on the device. Furthermore, Proofpoint Targeted Attack Protection’s threat intelligence help security teams stay ahead of attackers by detecting, analyzing, and blocking advanced threats. This includes advanced email threats delivered through malicious attachments and URLs, zero-day threats, polymorphic malware, fileless malware, weaponized documents, and phishing attacks. These capabilities complement Microsoft Defender for Endpoint, which delivers preventative protection, post-breach detection, automated investigation, and response.
The global data exfiltration techniques market was valued at $69,705.62 million in 2021, and is projected to reach $217,540.21 million by 2031, registering a CAGR of 12.3% from 2022 to 2031.
An increase in online malware and misuse of the internet, and the surge in the incidents of data loss in the on-premise environment are major growth factors for the market.
North America is the largest regional market for data exfiltration techniques market.
Barracuda Networks, Inc, DTEX Systems Inc., Exabeam, Fortra LLC, Fortinet, Inc., Juniper Netwroks, Inc., Pen Test Partners, Proofpoint, Tessian Limited, and Xorlab.
The key growth strategies include product portfolio expansion, acquisition, partnership, merger, and collaboration.
Loading Table Of Content...
Loading Research Methodology...


