Table Of Contents
- The Evolution of Cyber Warfare
- Digital Sphere, a Key Weapon in Modern Conflicts
- Fortifying Cybersecurity Measures
- Investors Intensifying the Industry Growth
- Key Innovators Crafting a Better Tomorrow
- Cyber Warfare: An Emerging Solution to Combat Cyber Threats
- Trailblazer of Warfare Technologies
- Evaluating the Penetration Rate of Cyber Warfare Technologies
- Potential Future Capabilities and Experts’ Forecast
- Cyber Warfare : A Boon or a Bane?

Onkar Sumant

Akshata Tiwarkhede
Cyber Warfare: The Fifth Dimension Battlefield

Cyber warfare is seen by nation–states as an affordable way to project power, wield influence, and accomplish strategic goals without using conventional military force. It involves the application of digital strategies to attack networks, data, and computer systems with the aim of espionage, disruption, or harm. Attackers use advanced technologies to target loopholes in digital infrastructure to obtain unauthorized access to private data or to interfere with essential business processes. Dr. Jean Renouf, the CEO of Safer Future, says “The nature of war is changing, so you don’t have to have two tanks shooting at each other to call it war.” Thus, cyber warfare is a transformation from using weapons in conflicts to radically shifting the nature of the wartime battlefield, representing an era of information war.
Malware distribution, phishing, denial-of-service, and social engineering techniques are majorly used to invade the digital sphere. However, to address this challenge, tools such as intrusion detection systems, firewalls, and antivirus software are used to guard against hostile activities and unauthorized access to networks and systems. Moreover, by transforming data into a safe format that is only accessible by authorized persons, encryption technologies guarantee the confidentiality and integrity of data. To enable more proactive and adaptable cyber defenses, AI and ML algorithms are used for behavior analysis, threat detection, and anomaly detection. In addition, to quickly detect patterns, trends, and possible security risks, big data analytics systems process and analyze massive volume of data. To further ensure safety, critical data is stored securely and decentralized using blockchain technology, which guarantees the immutability and integrity of the data.
The Evolution of Cyber Warfare
Although there is no clear date of when cyber warfare began, in March 1999, first known “internet war” in Kosovo hit cyberspace. The North Atlantic Treaty Organization (NATO) led a peace-support operation in Kosovo to protect the values on which the alliance was founded and not to conquer or preserve territory. NATO’s internet infrastructure was attached by numerous pro-Serbian hackers with the goal to disrupt military operations. The U.K. admitted to having lost some database information, whereas other states declared that the cyberattack had no impact on their overall war effort. Post this conflict, emerged precursors in the modern cyber warfare; for instance, cyberattacks in Estonia, Georgia, and Iran were reported in 2007, 2008, 2010, respectively. In addition, cyberattack on an election authority in the U.K. was reported in 2022, followed by a cyberattack on a telecommunications authority in India in 2023. The most recent incident involves a cyberattack on a media company in Ukraine. While cyber warfare is still in its infancy, with rapid technological advancements, it can be used not only against military forces but also against civilian targets. Leon Edward Panetta—retired American politician and government official who served as Secretary of Defense, director of the CIA, White House Chief of Staff, director of the Office of Management and Budget—described cyber warfare as “the most serious threat in the twenty-first century,” that has the capability to destroy the entire infrastructure and cripple the nation.
Digital Sphere, a Key Weapon in Modern Conflicts
Rising digitization of modern society and the sophistication of cyber threats are indicative of the market's evolving dynamics in cyber warfare. Technological advancements have led to the emergence of cyber warfare, with multiple state actors, military units, cybersecurity companies, and individual hackers actively participating in cyberattacks. In addition, advances in cyber warfare tactics and techniques have made it possible for attackers to breach networks & confidential data more precisely and efficiently. For instance, in February 2024, the FBI, CISA, and the Department of Health and Human Services (HHS) issued a warning to the U.S. healthcare organizations regarding targeted ALPHV/Blackcat ransomware attacks. BlackCat is exploiting the ScreenConnect vulnerability CVE-2024-1709 for initial access.

Although digitization has undeniably become a key aspect that offers enhanced convenience and efficiency, it is increasing the risk of cyber threats, making robust cyber security measures not only necessary but also imperative. As organizations and individuals alike rely heavily on digital platforms for communication, transactions, and storage of sensitive information, they inadvertently increase their vulnerability to cyberattacks. Thus, to effectively mitigate cyber threats and protect sensitive data, governments around the world have implemented various strategies to strengthen cybersecurity and are investing in comprehensive strategies.
Fortifying Cybersecurity Measures
The penetration of ML and AI in cyber security is one noteworthy advancement. These technologies assist companies in staying ahead of constantly changing cyberthreats by enabling automated threat identification, quick reaction times, and flexible defenses. Furthermore, increasing adoption of ransomware-as-a-service (RaaS) models, identification of flaws in widely used hardware and software, and rising state-sponsored cyber espionage operations aimed at government organizations and vital infrastructure are other noteworthy developments.
However, the quickly changing landscape of cyber threats is one of the major obstacles, necessitating ongoing innovation and adaptation to keep one step ahead of competitors. Furthermore, integration with other existing technologies is a consideration for cyber warfare. Innovations in critical infrastructure, for instance, cloud computing and Internet of Things (IoT) devices, create new attack surfaces that need to be secured with extensive security procedures.
For instance, in April 2023, Raytheon Technologies launched RAIVEN, a revolutionary electro-optical intelligent-sensing capability, which enables pilots to have faster and more precise threat identification. RAIVEN can identify objects optically and spectrally simultaneously in real time—a single electro-optical/infrared system has never been able to do this before. The intelligent sensing capability of RAIVEN uses AI, hyperspectral imaging, and LiDAR to enable operators to see up to five times farther and clearer than traditional optical imaging. This helps increase platform survivability and gives the warfighter decision advantage over peer threats. Governments around the world have implemented various initiatives to strengthen cybersecurity in response to the increasing threats posed by cyberattacks. For example, the U.S. has established the Cybersecurity and Infrastructure Security Agency (CISA) to enhance the nation's cybersecurity measures through threat intelligence sharing, incident response coordination, and cybersecurity awareness programs. In the European Union, the European Cybersecurity Agency (ENISA) works to improve cybersecurity capabilities across member states through collaboration, research, and the development of cybersecurity standards. In addition, the countries such as Japan and Australia have introduced national cybersecurity strategies that prioritize the protection of critical infrastructure, data privacy, and the resilience of digital systems against cyber threats.
Thus, cyber warfare technology requires a number of technological, commercial, and social breakthroughs to reach its full potential. The advent of cutting-edge technologies such as quantum computing, AI, and ML is further spurring interest in cyber warfare capabilities. These technologies improve both offensive and defensive operations by enabling quicker threat identification, more precise targeting, and increased automation of cyberattacks.
Investors Intensifying the Industry Growth
Governments, military institutions, and commercial enterprises are heavily investing in cyber warfare capabilities to defend against cyberattacks, secure critical data, and preserve a strategic advantage in cyberspace. For instance, in 2018, the United States Department of Defense announced a significant increase in its budget allocation for cybersecurity initiatives, focusing on enhancing its cyber capabilities, improving information sharing among agencies, and developing advanced technologies to counter cyber threats. Similarly, the countries like China and Russia have been investing heavily in cyber capabilities, including the development of defensive cyber weapons, cyber espionage capabilities, and cyber defense mechanisms to protect their national interests and critical infrastructure from cyberattacks.
Moreover, commercial enterprises have been ramping up their investments in cybersecurity technologies and services to secure their digital assets, customer data, and intellectual property. Companies across various industries, such as finance, healthcare, and technology, have been allocating resources to strengthen their cybersecurity posture by deploying advanced threat detection systems, implementing encryption protocols, and conducting regular security audits to identify and mitigate vulnerabilities in their networks and systems.
Thus, to successfully address new threats and establish resilient cyber defenses, it is essential to invest in cybersecurity education and workforce development, promote information sharing and collaboration among stakeholders, and cultivate a culture of cybersecurity awareness.
Key Innovators Crafting a Better Tomorrow
The government intelligence agencies such as the People's Liberation Army (PLA) in China, the Government Communications Headquarters (GCHQ) in the UK, and the National Security Agency (NSA) in the U.S notably contribute toward the shifting landscape of market dynamics. For instance, in March 2024, IBM launched the IBM X-Force Cyber Range in the heart of Washington DC to help federal agencies improve their resilience against these evolving threats. This new state-of-the-art center demonstrates IBM’s commitment to both the federal market and helping to secure the nation’s critical infrastructure, while concurrently serving their corporate clients. The X-Force Cyber Range aims to help clients strengthen their cross-organization response to these threats in a safe and fault-free environment. The range introduces new custom training exercises designed specifically to help U.S. federal agencies, their suppliers, and critical infrastructure organizations more effectively respond to increasingly persistent and disruptive cyberattacks and future threats posed by AI.
Moreover, the development of cyber warfare capabilities is significantly aided by the military organizations, including the Russian GRU Main Centre for Special Technologies (GTsST) and the U.S. Cyber Command (USCYBERCOM). Many cybersecurity companies, in addition to governmental and military organizations, are focused on developing cutting-edge technologies for cyber warfare. A variety of goods and services are available from businesses such as Palo Alto Networks, FireEye, and CrowdStrike that are intended to identify, stop, and lessen cyberattacks.
For instance, in April 2023, Cisco Systems, Inc. enhanced its cyber security portfolio and updated the latest progress toward its vision of the Cisco Security Cloud, a unified, AI-driven, cross-domain security platform. The launch of new XDR solution of Cisco and the release of advanced features for Duo MFA are expected to help organizations better protect the integrity of their entire IT ecosystem.

Cyber Warfare: An Emerging Solution to Combat Cyber Threats
- Rapid digitization of vital infrastructure, escalation of geopolitical tensions, and sophistication of cyber threats have all contributed to the development in cyber warfare technologies in recent years. Cyber warfare technology is used in a variety of settings, such as business espionage, political influence campaigns, military operations, and information collection. Cyber warfare strategies and techniques are primarily employed by state entities, military organizations, cyber threat intelligence agencies, and cybercriminal gangs. For instance, in December 2023, IBM signed a contract with the NATO Communications and Information Agency (NCI) to help strengthen the Alliance's cybersecurity posture with improved security visibility and asset management across all NATO enterprise networks. Initiated in January 2024, IBM Consulting Cybersecurity Services will be delivering a custom-made, performance-based asset, configuration, patching, and vulnerability (ACPV) management service to the Alliance.
- In recent years, countries have increasingly adopted cyber warfare tactics as a defensive solution to disrupt or dismantle the online infrastructure of terrorist organizations for the well-being and safety of the nation. Governments aim to weaken the operational capabilities of these groups and prevent them from carrying out attacks by targeting their communication networks, financial systems, and propaganda-generating channels. For instance, intelligence agencies are employing sophisticated cyber espionage techniques to infiltrate terrorist networks, gather intelligence on their activities and plans, and disrupt their online operations. This could involve hacking into their websites, social media accounts, and communication channels to monitor their movements and intercept communications. Moreover, political players strategically employ cyber warfare tactics to facilitate secure & transparent elections and ensure the integrity of democratic processes while safeguarding against external interference and misinformation campaigns.
- Political players also employ cyberwarfare tactics strategically to facilitate secure and transparent elections, ensuring the integrity of democratic processes while safeguarding against external interference and misinformation campaigns.
Thus, by leveraging cyber warfare tactics in this manner, countries can effectively combat terrorism, protect their citizens from harm, and contribute to global security and stability.
Trailblazer of Warfare Technologies
Defense and intelligence agencies, whose governments and military groups have made significant investments in building cyber capabilities, serve as the early adopters of cyber warfare technologies. Furthermore, the high-value asset industries, including banking, energy, telecommunications, and healthcare have adopted cyber warfare strategies at an early stage to defend vital infrastructure from cyberattacks. The defense and intelligence industry has long been recognized as an early adopter of cyber warfare capabilities, leveraging technology to gain a strategic advantage in the digital domain. One of the earliest developments is the establishment of the National Security Agency's (NSA) Tailored Access Operations (TAO) unit in 1980s. TAO was set up to conduct advanced cyber operations, including offensive cyberattacks and intelligence gathering, making it one of the pioneering units in the field of cyber warfare.
In more recent times, the defense and intelligence industry has continued to lead the way in adopting cutting-edge cyber warfare technologies and tactics. For instance, in June 2015, the United States Cyber Command (USCYBERCOM) announced the establishment of Cyber Mission Forces, specialized teams dedicated to conducting cyberspace operations to defend against cyber threats, support military missions, and protect critical infrastructure. These forces are equipped with advanced tools and expertise to detect, deter, and respond to cyberattacks in real time, showcasing the industry's commitment to stay ahead in the cyber warfare domain.
In March 2022, L3Harris Technologies partnered with venture capital firm, Shield Capital to foster emerging defense and commercial technologies that address customers’ growing requirements for innovative, agile solutions that can be rapidly fielded. The agreement provides L3Harris access to disruptive innovators for technology transfer, teaming arrangements, direct investments or potential acquisitions and partnered contracts. Working with Shield Capital is a part of the company’s strategy to leverage third-party capabilities and make calculated investments to address customers’ most urgent and difficult national security challenges.
Evaluating the Penetration Rate of Cyber Warfare Technologies
Adoption of cyber warfare technologies is anticipated to increase across numerous sectors and applications as cyber threats continue to evolve. This covers industries where digital transformation efforts have led to a higher reliance on networked systems and data-driven technology, including manufacturing, transportation, retail, and education. For instance, in February 2024, the National Security Agency (NSA)—an intelligence agency of the United States Department of Defense—partnered with Cybersecurity and Infrastructure Security Agency (CISA) to issue a Cybersecurity Advisory (CSA) to address People’s Republic of China (PRC) of targeting the U.S. critical infrastructure. The CSA entitled “PRC State-Sponsored Actors Compromise and Maintain Persistent Access to U.S. Critical Infrastructure” is led by the Cybersecurity and Infrastructure Security Agency (CISA) in partnership with NSA, the Federal Bureau of Investigation (FBI), and additional government agencies.
Furthermore, by leading the way in innovation, technology, and different strategies, these agencies set the standard for cybersecurity practices, threat detection, and response strategies. Their proactive approach to cybersecurity will drive continuous evaluation and improvement in the field, influencing industry standards, boosting collaboration and enhancing global cybersecurity resilience. As industries continue to shape the future by staying ahead of emerging threats, leveraging cutting-edge technologies and safeguarding national security interests in an increasingly complex and interconnected digital landscape.
For instance on February 2024, the U.S. Department of Energy (DOE) announced $45 million to 16 projects across six states to protect the nation’s energy sector from cyberattacks. Managed by DOE’s Office of Cybersecurity, Energy Security, and Emergency Response (CESER), selected projects will help develop new cybersecurity tools and technologies designed to reduce cyber risks and strengthen the resilience of America’s energy systems, which include the power grid, electric utilities, pipelines, and renewable energy generation sources like wind or solar.
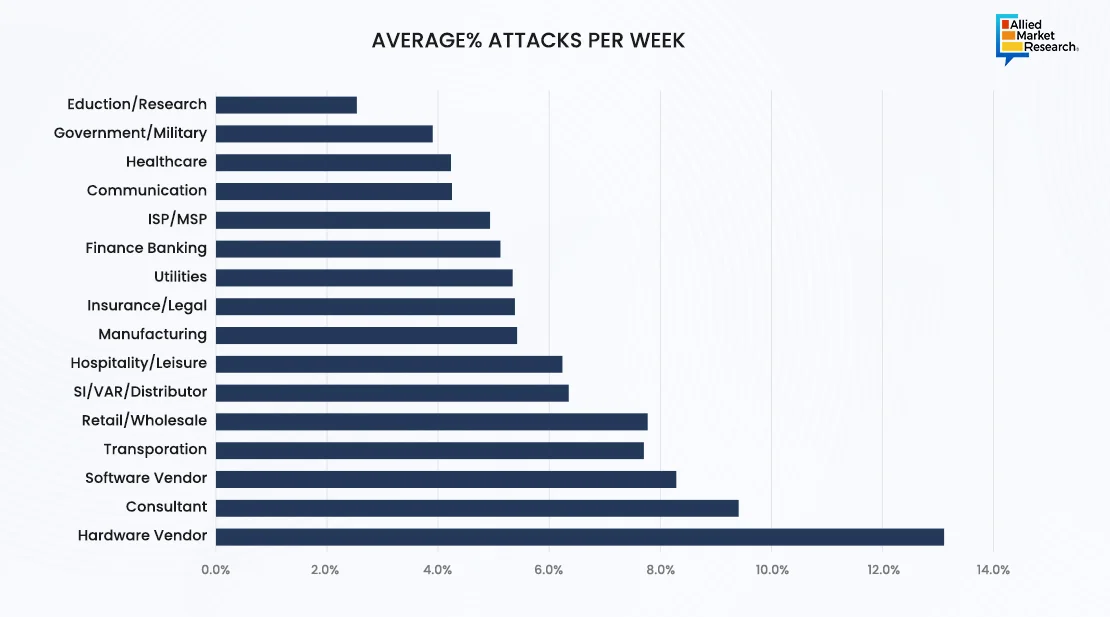
According to the Checkpoint and vpnAlert reports, education/research industry faces 13.1% with 2,314 number of average attacks per week. In recent years, the education and research industry has become a prime target for cyberattacks, with numerous high-profile incidents highlighting the sector's vulnerability. For instance, in 2022, the University of California, San Francisco (UCSF), fell victim to a ransomware attack where hackers demanded a $1.14 million ransom. The attack crippled the university's systems, disrupting crucial research projects and patient care operations. Similarly, in 2023, the UK's National Health Service (NHS) faced a significant data breach affecting medical research data stored on its systems. These incidents underscore the critical importance of cybersecurity in safeguarding not only academic research but also public health and safety. Thus, to foster a culture of cyber awareness among staff and students, immediate action is required in response to the growing cyberattacks targeting the research and education sectors. This can be achieved by investing in advanced mechanisms such as AI in defense and security.
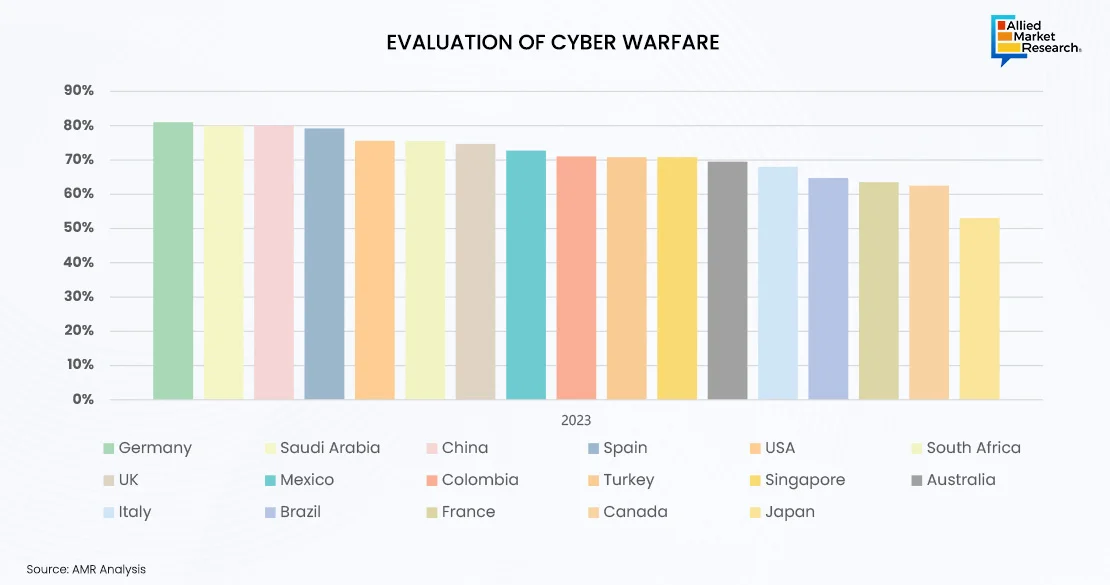
Germany has been experiencing the highest weekly rate of 81% cyberattacks, followed by Saudi Arabia, while Canada and France have encountered the fewest cyber incidents. These cyberattacks are triggered due to various factors such as their significant economic and political influence, advanced technological infrastructure, and geopolitical importance.
Germany, as a leading economic power in Europe with advanced technological infrastructure, became a prime target for cyber criminals seeking to exploit vulnerabilities for financial gain or data theft. According to a report by the German Federal Office for Information Security (BSI), Germany experienced a record 197 million cyberattacks in 2023, a significant increase compared to previous years. The country's interconnected networks, critical industries, and government institutions made it an potential target for cyber adversaries. In addition, Saudi Arabia, a key player in the Middle East with strategic importance in global affairs, faced a surge in cyber incidents in 2023. The Saudi National Cyber Security Center reported over 230,000 cyberattacks targeting various sectors, including energy, finance, and government agencies. The country's reliance on digital infrastructure for economic development and its geopolitical significance made it a priority target for threat actors seeking to cause disruption, steal valuable data, or engage in political espionage.
Hence, the alarming number of cyberattacks in Germany and Saudi Arabia in 2023 underscores the growing sophistication and persistence of cyber threats. As cyber defenses continue to evolve, proactive measures such as enhanced threat intelligence sharing and investment in cybersecurity resilience are necessary to mitigate the risks posed by malicious actors in the digital realm.
Potential Future Capabilities and Experts’ Forecast
The future of the cyber warfare market is marked by the development of new applications and capabilities driven by advancements in technology, evolving threat landscapes, and shifting geopolitical dynamics. Navigating this swiftly changing environment demands an understanding of projected future changes, forecasts, critical innovations, and related hazards.
Moreover, cyber adversaries have new attack surfaces and opportunities due to the growth of critical infrastructure networks and the rapid penetration of IoT devices. Cyber warfare technologies may be used in the future to attack connected healthcare systems and autonomous cars as well as to target IoT ecosystems and interfere with smart city infrastructure. Furthermore, by enabling attackers to crack encryption techniques, breach secure communication channels, and threaten the integrity of digital signatures, advances in quantum computing have the potential to completely transform cyber warfare. Future cyber defense plans are anticipated to include quantum-safe cybersecurity technologies and quantum-resistant cryptography as key elements.
Although precise forecasts vary, experts generally predict that in the upcoming years, cyber warfare technologies will continue to develop and be widely adopted. The primary objectives of development roadmaps are to augment both offensive and defensive capabilities, optimize channels for exchanging threat intelligence, and promote global collaboration to jointly tackle worldwide cyber threats. The increasing digitization of vital infrastructure; the growing attack surface of interconnected systems; and the increasing reliance on cyberspace for political, military, and economic operations are the factors that could lead to mainstream adoption.
Cyber Warfare : A Boon or a Bane?
Cyber warfare technology presents serious risks and concerns in addition to its potential benefits. These include the possibility for devastating cyberattacks on vital infrastructure, interruption of services that are necessary, theft of confidential data, and intensification of cyber warfare between states. Although cyber warfare tactics serve as a threat, they can be leveraged to gain advantage or contribute to the well-being of a nation. For instance, stronger cybersecurity defenses, promotion of international agreements and norms for appropriate behavior in cyberspace, improved public–private partnerships for the sharing of threat intelligence, and the development of strong incident response capabilities to lessen the impact of digital attacks are a few of the many strategies needed to address serious threat risks. Creating standards for quantum-resistant cryptography, implementing secure-by-design in IoT devices, developing AI and ML algorithms for threat detection and response, and creating strong cybersecurity laws and guidelines will help shape the future of the cyber warfare industry in the coming future.
For further insights, get in touch with AMR analysts.

