The Evolution and Impact of Cyberwarfare: Understanding the Digital Battlefield

Cyberwarfare has significantly evolved since the inception of the Internet, showing how digital attacks have grown in complexity and skill. The roots of cyberwarfare can be traced back to the late 20th century, with one of the earliest notable incidents being the Morris Worm in 1988. Created by a Cornell University student, the worm caused extensive damage by infecting approximately 10% of the computers connected to the Internet at the time, leading to repair costs estimated between $10 million and $100 million.
According to Cybersecurity Ventures, cybercrime is expected to cost the world $6 trillion annually in 2021. This translates to $500 billion per month, $115.4 billion per week, $16.4 billion per day, $684.9 million per hour, $11.4 million per minute, and $190,000 per second.
These figures highlight the immense financial impact of cybercrime globally and underscore the need for robust cybersecurity measures.

As the Internet expanded, so did the scope and impact of cyber-attacks. In 2007, Estonia experienced a large-scale cyber assault following a political dispute with Russia. This attack, which targeted government, banking, and media websites, demonstrated the potential of cyberwarfare to disrupt national infrastructure. The incident marked a significant turning point, highlighting the need for robust cybersecurity measures.
The 2008 Russo-Georgian War provided another significant example of cyberwarfare in action. During the conflict, Georgian government websites were hit by DDoS attacks, disrupting communication and spreading disinformation. This event highlighted the strategic use of cyber-attacks alongside traditional military operations.
One such widely known attack is Stuxnet, discovered in 2010. A joint effort by the United States and Israel, Stuxnet targeted Iran's nuclear facilities, specifically the Natanz uranium enrichment plant. By sabotaging centrifuges, Iran's nuclear program was significantly delayed. This was the first time a cyber weapon caused physical damage, setting a precedent for future cyber operations.
In the last few years, cyberwarfare has evolved, with countries and other groups using more advanced tactics. For example, the 2016 U.S. presidential election faced claims of Russian interference through hacking and spreading false information. This event highlighted the potential of cyber-attacks to influence political processes and public opinion on a global scale.
More recently, in 2023, Australia's government expressed deep concern over a cyberattack attributed to Iran's Islamic Revolutionary Guard Corps (IRGC). The attack aimed to extort data from an Australian organization, demonstrating the ongoing threat posed by state-sponsored cyber activities.
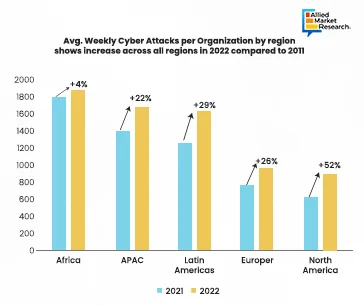
In 2022, global cyberattacks surged by 38%, with Africa experiencing the highest number of weekly attacks per organization at 1,875. The Asia-Pacific region experienced 1,691 weekly attacks. North America saw a 52% increase, Latin America 29%, and Europe 26%. The education sector faced the most cyberattacks, with healthcare also seeing a significant rise. Smaller, agile hacker groups exploited remote work tools and targeted educational institutions.
Cyberwarfare has grown with our reliance on digital infrastructure, making cybersecurity essential. With the advancement of technology, there have been constant updates and new defense strategies to counter new threats.
Dynamics in Cyberwarfare
The landscape of cyberwarfare is dominated by several key players, including nation-states and hacking groups with varying motivations and tactics. They operate with a blend of political, economic, and military objectives, and their activities have shaped the dynamics of global cyber conflict.
Nation-States
China stands out as a leading player in cyber espionage and cyberwarfare. Chinese state-sponsored groups like APT10 (also known as Stone Panda) have been implicated in extensive cyber espionage activities, targeting critical sectors such as defense, technology, and healthcare globally. In March 2023, a Chinese cyber espionage group targeted government entities in Vietnam, Thailand, and Indonesia using advanced malware designed to evade detection.
Russia is another major player in cyberwarfare, known for its sophisticated cyber capabilities. Russian state-sponsored groups, such as APT29 (Cozy Bear) and APT28 (Fancy Bear), have been involved in numerous high-profile cyber operations. For instance, during the Russia-Ukraine conflict, Russian hackers launched social engineering campaigns targeting U.S. and European politicians and businesspeople, aiming to manipulate public opinion and discredit anti-Putin statements. Moreover, Russian cyber activities often extend to disrupting critical infrastructure, as seen in the attack on Poland's tax service website in February 2023.
North Korea employs cyber operations to gather intelligence, conduct attacks, and generate revenue, often through cryptocurrency theft. In January 2023, the FBI attributed a $100 million cryptocurrency heist from Harmony's Horizon Bridge to North Korean hackers. Groups like the Lazarus Group are notorious for their involvement in major cyber incidents, including the Sony Pictures hack in 2014 and the WannaCry ransomware attack in 2017.
Iran has increasingly utilized its cyber capabilities for both regional and global influence. Iranian state-sponsored groups have targeted various sectors, including IT, infrastructure, and government. For example, in February 2023, Iranian hackers disrupted a state-run television broadcast during a speech by Iranian President Ebrahim Raisi, airing antigovernment slogans. Additionally, Iranian groups often employ spear-phishing tactics to gain initial access to targeted networks.
Prominent Hacking Groups
Apart from nation-states, various hacking groups have gained prominence due to their sophisticated operations and significant impacts.
OceanLotus (APT32), a Vietnam-based group, has been active since 2012, focusing on cyber infiltration targeting organizations of interest to the Vietnamese government. They have been known to target human rights and research institutes, as well as the Chinese government during the COVID-19 pandemic.
APT36, aligned with Pakistan, primarily targets Indian government personnel and Pakistani political opposition. This group uses social engineering to trick targets into installing remote access trojans, facilitating data theft.
Lazarus Group, linked to North Korea, is infamous for its high-profile cyber-attacks aimed at financial gain and strategic disruption. The group's activities range from cyber espionage to large-scale financial heists, exemplified by their involvement in the Sony Pictures hack and the WannaCry ransomware attack.
Convergence of Cyber and Influence Operations
The convergence of cyber operations and influence campaigns has become more pronounced, particularly in the context of geopolitical conflicts. During the Russia-Ukraine war, the coordination between cyber-attacks and influence operations has been evident, with cyber-enabled influence campaigns maturing rapidly. This convergence allows state actors to amplify the disruptive effects of their operations, manipulating public perception and destabilizing adversaries.
Knowing the key players and their tactics is important for creating strong cyber defenses and promoting international cooperation to reduce cyberwarfare threats. As technology evolves, the methods and motivations of these actors will continue to adapt, necessitating ongoing innovation in cybersecurity measures.
Tactics and Techniques in Modern Cyberwarfare
Cyberwarfare tactics and techniques have become increasingly sophisticated, involving a range of strategies designed to infiltrate, disrupt, and manipulate digital and physical infrastructures. Understanding these methods is essential for developing effective countermeasures.
Social Engineering and Phishing Attacks
Social engineering remains one of the most effective tactics used in cyberwarfare. It involves tricking people into sharing confidential information or doing things that compromise security. A prominent example is the phishing campaigns conducted by Russian hacking groups like APT29 (Cozy Bear) and APT28 (Fancy Bear), which often use highly convincing emails to trick victims into clicking malicious links or downloading malware. These techniques have been used extensively in targeting political entities and influencing elections.
Malware and Ransomware
Malware, including ransomware, is a key tool in cyberwarfare. Ransomware attacks encrypt a victim's data and demand a ransom for its release. The 2021 Colonial Pipeline ransomware attack by the DarkSide group, believed to be linked to Russian state actors, is a notable example. This attack disrupted fuel supplies across the U.S. East Coast, highlighting the potential for ransomware to cause significant economic and operational damage.
Denial-of-Service (DoS) Attacks
DoS and Distributed Denial-of-Service (DDoS) attacks aim to overwhelm and disable targeted systems by flooding them with traffic. For instance, a DDoS attack caused a seven-hour internet outage affecting public healthcare institutions in Singapore in November 2023. The attack overwhelmed servers with excessive traffic, disrupting access to websites, emails, and productivity tools.
Advanced Persistent Threats (APTs)
APTs involve prolonged and targeted cyber intrusions, often by state-sponsored groups. These attacks aim to steal data, disrupt operations, or establish a persistent presence within networks. The 2014-2016 attack on Ukrainian artillery units by the Russian group Fancy Bear, which used malware embedded in an Android application, exemplifies an APT operation that resulted in substantial military losses for Ukraine.
Supply Chain Attacks
Supply chain attacks target vulnerabilities in third-party software or hardware providers to infiltrate larger organizations. The 2020 SolarWinds attack by Russian APT29 exploited a software update to insert malicious code, affecting multiple U.S. government agencies and private companies. This attack highlighted the risks associated with interconnected digital ecosystems and the importance of securing supply chains.
Propaganda and Information Warfare
Cyberwarfare also includes propaganda and information operations designed to influence public perception and destabilize societies. During the 2016 U.S. presidential election, Russian operatives used social media platforms to spread disinformation and create divisions among the electorate. These campaigns often complement cyber-attacks, amplifying their impact and achieving broader strategic objectives.
Cyber Espionage
Cyber espionage involves stealing sensitive information from governments, corporations, or individuals. Chinese state-sponsored groups, for example, have conducted extensive cyber espionage campaigns targeting various sectors. In 2023, a Chinese cyber espionage group targeted government entities in Southeast Asia using advanced malware to evade detection and gather intelligence.
Economic Disruption
Cyber-attacks targeting economic systems can cause significant disruption. Attackers may target stock markets, payment systems, or banks to steal money or block access to funds. These attacks can undermine economic stability and erode public trust in financial institutions.
Understanding these tactics and techniques is important for developing robust cybersecurity defenses and mitigating the impacts of cyberwarfare. As cyber threats keep changing, our strategies to counter them must also evolve, requiring constant adaptation.
Building Cyber Resilience: Strategies for Defense and Continuity
In the ever-evolving landscape of cyberwarfare, building strong cyber defenses and resilience has become highly important. Cyber resilience is not just about preventing attacks but also about ensuring that organizations can continue operating during and after a cyber incident. This approach combines technological defenses with strategic planning to withstand, recover from, and adapt to adverse cyber conditions.
Proactive Defense Strategies
A key aspect of cyber defense is the adoption of proactive measures to mitigate potential threats. The U.S. Department of Defense (DoD) emphasizes a "defend forward" strategy, which involves disrupting malicious cyber activities before they impact the U.S. homeland. This approach is part of the DoD's 2023 Cyber Strategy, which highlights the need for innovative and evolving defense mechanisms to stay ahead of cyber threats.
Collaboration and Public-Private Partnerships
Effective cyber defense requires collaboration between governments, private sectors, and international partners. NATO's cyber defense initiatives underline the importance of collective defense and security in the Euro-Atlantic zone. NATO stresses the need for member states to work together to boost their resilience against widespread cyber threats.
Public-private partnerships are also crucial in building cyber resilience. The Microsoft Digital Defense Report 2023 points to increased intelligence sharing between public and private sectors as a key factor in enhancing responses to cyber threats. By leveraging the strengths of both sectors, organizations can develop more comprehensive defense strategies and improve their resilience to cyber-attacks.
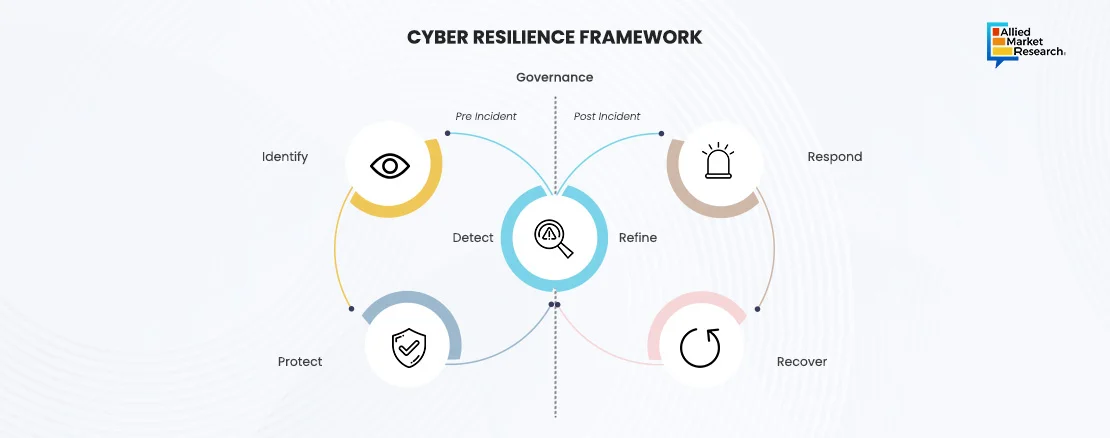
Cyber Resilience Frameworks
Cyber resilience frameworks integrate various elements of cybersecurity to ensure continuous operation and swift recovery from cyber incidents. The concept of cyber resilience goes beyond traditional defensive measures, focusing on maintaining core functions and adapting to evolving threats. In today's digital world, where threats are quite certain and more advanced, having a dual focus is essential.
For instance, implementing least privileged access controls, regular posture management, and automatic cloud backups are essential components of a resilient cyber infrastructure. These measures help organizations mitigate risks, maintain operational continuity, and recover swiftly from breaches. The increase in password attacks and business email compromise (BEC) incidents points out the need for robust access controls and proactive threat management.
Moreover, InConsult's framework for achieving cyber resilience focuses on building robust systems to anticipate, withstand, recover from, and adapt to cyberattacks.
Key elements are proactive governance, risk identification, implementing protective controls, continuous monitoring, effective incident response, and thorough recovery plans. This approach aims to ensure that organizations can maintain critical operations and protect data integrity despite cyber threats. The framework emphasizes the importance of constantly improving and adapting to new cyber risks to boost overall resilience.
Leadership and Organizational Culture
Leadership plays a pivotal role in shaping an organization's cyber resilience. Effective leaders ensure that cyber resilience is a part of every decision and action. This involves not only having a technically sound cybersecurity team but also ensuring that cybersecurity is a regular topic in boardroom discussions. Proactive leaders invest in continuous education, stay informed about emerging threats, and adapt their strategies to remain a step ahead of potential risks.
By combining technological solutions with strategic leadership and collaborative efforts, organizations can build a resilient defense against the growing threats of cyberwarfare. This holistic approach ensures that they are not only prepared for inevitable breaches but also capable of sustaining operations and recovering swiftly in the face of adversity.
Case Study: The Viasat Cyber Attack
One of the most significant cyberwarfare incidents in recent years is the Viasat cyber-attack, which occurred on February 24, 2022, coinciding with Russia's invasion of Ukraine. This attack, attributed to the Russian military intelligence agency GRU, disrupted broadband satellite internet access provided by Viasat's KA-SAT network, affecting thousands of users across Ukraine and Europe.
Impact and Scope
The attack targeted Viasat's satellite modems, rendering them inoperable and causing widespread internet outages. The disruption primarily affected critical infrastructure and communication services in Ukraine, hampering the country's ability to coordinate defenses and manage emergency responses during the initial stages of the invasion. The attack also had a significant spillover effect, impacting various European countries that relied on Viasat's services.
Attribution and Response
The European Union, the United Kingdom, and the United States publicly attributed the cyber-attack to Russia, highlighting it as part of Russia's broader strategy to destabilize Ukraine and its allies. This attribution was based on technical analysis and intelligence sharing among these nations. The coordinated response included condemning Russia's actions and reinforcing the importance of cyber defense and resilience among NATO allies and other partners.
Legal and Strategic Implications
The Viasat attack highlighted the urgent need for strong international laws to tackle state-sponsored cyber activities. The incident also showed up gaps in existing international laws and norms governing cyber warfare, prompting discussions on enhancing legal mechanisms to hold perpetrators accountable and protect critical infrastructure.
Additionally, the attack demonstrated the importance of integrating cyber operations into broader military strategies. Effective cyber defense requires a combination of technical measures, strategic planning, and international collaboration. The Viasat incident emphasized the need for countries to develop comprehensive cyber defense strategies that include real-time threat detection, incident response capabilities, and resilient infrastructure to mitigate the impact of such attacks.
Lessons Learned
The Viasat cyber-attack taught several important lessons for improving cyber resilience:
Proactive Defense: Nations must adopt proactive defense strategies to detect and mitigate cyber threats before they cause significant damage.
Collaboration: International cooperation and intelligence sharing are crucial for attributing cyber-attacks and coordinating effective responses.
Legal Frameworks: Strengthening international legal frameworks can help address state-sponsored cyber activities and protect critical infrastructure.
Resilient Infrastructure: Developing resilient cyber infrastructure that can withstand and quickly recover from attacks is essential for maintaining operational continuity during crises.
The Viasat cyber-attack serves as a stark reminder of the evolving nature of cyber warfare and the need for continuous adaptation and vigilance in defending against such threats.
The Future of Cyberwarfare
The future of cyberwarfare is expected to witness an increased use of advanced technologies like artificial intelligence and quantum computing, making attacks more sophisticated and harder to detect. With the growing number of cyber-threats, the cybersecurity market is projected to grow significantly, driven by the need for advanced security solutions and robust defense mechanisms. Companies and governments are investing heavily in cybersecurity to protect critical infrastructure and maintain national security.
Allied Market Research delves into the expansive cybersecurity market, providing thorough analyses of technological advancements, market dynamics, and regulatory landscapes shaping the field. Our comprehensive reports offer stakeholders valuable insights into how the cybersecurity market is evolving. These insights help businesses capitalize on opportunities, innovate, and implement robust security practices in the cybersecurity industry. Contact our experts today for a detailed analysis of the drivers of growth and investment opportunities in cybersecurity!



