Automated Breach and Attack Simulation Market Insights, 2031
The global automated breach and attack simulation market was valued at USD 305.6 million in 2021, and is projected to reach USD 5.5 billion by 2031, growing at a CAGR of 33.6% from 2022 to 2031.
Increase in complexities in managing security threats and surge in demand for prioritizing security investments boost the growth of the global automated breach and attack simulation market. In addition, rise in number of cyber-attacks across the globe is positively impacting the growth of the automated breach and attack simulation market. However, lack of skilled security experts and lack of awareness related to advanced cybersecurity technologies hamper the automated breach and attack simulation market growth. On the contrary, rise in digitalization initiatives is expected to offer remunerative opportunities for the expansion of the automated breach and attack simulation market during the forecast period.

Automated breach and attack simulation solutions are the platforms or tools that enable security assessment automation by simulating real-world attack scenarios. These solutions help end-users identify loopholes in the existing security infrastructure and improve data protection. Moreover, ABAS is an automated process that simulates real-world cyberattacks and helps organizations to understand their security posture and identify potential weaknesses.
Segment Review
The automated breach and attack simulation market is segmented on the basis of offering, deployment mode, application, end user, and region. On the basis of offering, the market is bifurcated into platform and tools, and service. On the basis of deployment mode, the market is fragmented into on-premise, and cloud. On the basis of application, the market is categorized into configuration management, patch management, threat management, and others. By end user, the market is classified into enterprise and data centers, and managed service providers. By region, the market is analyzed across North America, Europe, Asia-Pacific, and LAMEA.
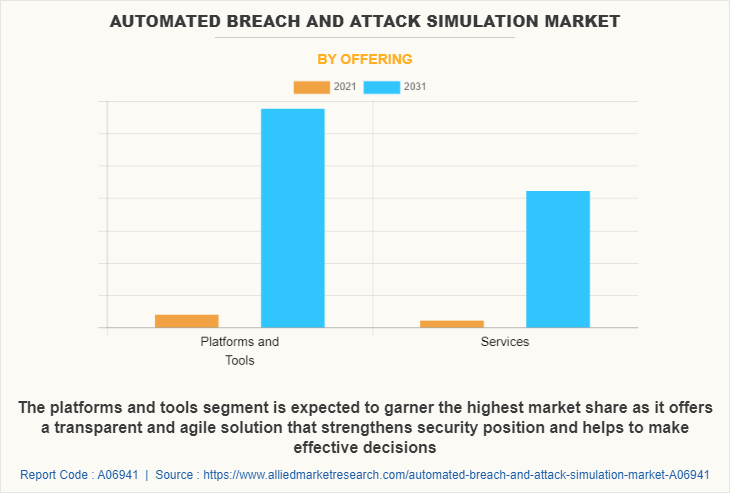
In terms of offering, the platforms and tools segment holds the largest automated breach and attack simulation market share owing to rise in incidences of insider attacks across the globe. However, the service segment is expected to grow at the highest rate during the forecast period owing to increase in need for organizations to understand and improve human behavior.
Region wise, the automated breach and attack simulation market size was dominated by North America in 2021 and is expected to retain its position during the forecast period, owing to the presence of major players that offer advanced solutions and invest heavily in solutions such as 5G, and IoT technologies. However, Asia-Pacific is expected to witness significant growth during the forecast period, owing to rapid advances in artificial intelligence, increase in usage of internet of things (IoT) devices.
The key players that operate in the automated breach and attack simulation industry market include AttackIQ, Keysight Technologies, Qualys, Inc., Rapid7, Sophos Ltd., Cymulate, FireMon, LLC., SafeBreach Inc., Skybox Security, Inc, Skybox Security, Inc, and XM Cyber. These players have adopted various strategies to increase their market penetration and strengthen their position in the automated breach and attack simulation industry.
Top Impacting Factors
Increase in Complexities in Managing Security Threats
Automated breach and attack simulation platform helps in finding security gaps from a variety of sources. In addition, organizations are investing a significant amount of their IT budgets and resources in implementing and measuring security. Moreover, continuous and fast growth in the adoption of digital business can be observed across the world, increasing number of solutions relying on applications. However, there have been no such solutions, which can resolve all applications security related problems. The simulated platform does resolve the issues and help search for vulnerabilities from the system. Furthermore, developers can easily safeguard the enterprise system from identified vulnerabilities, post detection of any vulnerability.
Increase in Demand for Prioritizing Security Investments
Prioritizing security investments is an ever-evolving industry, and opportunities regularly. The industry is expected to witness new opportunities for international investment as well as new types of alternatives to invest in. In addition, in recent years, it has become international market, creating new opportunities to use strategies that have already run their course in the U.S. Moreover, a 2022 survey by PwC Global Digital Trust Insights found that 65% of the private investors surveyed were planning on maintaining or increasing their allocation to cybersecurity investments over the next 12 months.
Furthermore, many investors are using security investments. This asset class helps to protect their sensitive data, intellectual property, and reputation. Moreover, as technology becomes an increasingly integral part of business operations, the security of digital assets is becoming critical to ensure business continuity and avoid disruptions to operations. This is particularly important for organizations that operate critical infrastructure, such as power grids, banking systems, and transportation networks, as a cyber-attack on one of these systems could have far-reaching consequences. Therefore, investors are enabling ABAS to have a security investment during the pandemic, which in turn is driving the growth of the market.
Digital Capabilities
Automated breach and attack simulation (BAS) technologies involve the use of digital tools and techniques to simulate real-world cyber-attacks for the purpose of testing and validating an organization's security defenses. Some of the digital technologies used in BAS include automated validation platforms, digital risk protection (DRP) tools, and attack emulation tools. These tools emulate the tactics, techniques, and procedures (TTPs) typically used by cyber attackers to identify vulnerabilities and weaknesses in an organization's security defenses. GreyMatter Verify is an example of an attack emulation tool used for BAS. Moreover, digital technologies play a critical role in automated breach and attack simulation by enabling organizations to identify vulnerabilities and weaknesses in their security defenses and develop and maintain effective cyber resilience strategies
Key Benefits:
Automated breach and attack simulation has several benefits for organizations including, improved security posture allows organizations to identify and address security vulnerabilities before they can be exploited by attackers. This helps to improve the overall security posture of the organization. Realistic testing, which helps to simulate real-world attack scenarios, giving organizations a better understanding of the way they would fare in an actual cyberattack. This allows security teams to identify weaknesses in their defenses and take steps to address them.
Moreover, automated breach and attack simulation can be more cost-effective than traditional manual testing methods which can be time-consuming and require significant resources. Furthermore, automated breach and attack simulations can also be used for staff training purposes. They can help employees better understand cybersecurity threats, which can help to improve the overall security culture of the organization.
Government Regulations:
All well-governed industries should be able to demonstrate due diligence to ensure regulatory compliance in applicable fields, including IT. Organizations are increasing adoption of advanced electronics heavily influenced by COVID-19. In addition, federal and state governments are improving their track plans for various privacy laws, which are applicable for data that are involved in their operations. For instance, the Gramm-Leach-Bliley Act not only covers banks but also securities firms and insurance companies, and companies providing many other types of financial products and services.
For instance, in March 2022, U.S. and European Commission announced New Trans-Atlantic Data Privacy framework to put in place new safeguards to ensure that signals surveillance activities are necessary and proportionate in the pursuit of defined national security objectives. Furthermore, the GDPR Act imposed by the European Government mitigates the risk of cyber security and any potential data breaches. Emerging countries of Asia-Pacific are developing stringent regulations, which comprise privacy, government regulatory environment, and intellectual property protection. For Instance, in August 2018, NICE acquired Mattersight Corporation The finalization of this deal brings together the market’s leading behavioral analytics and cloud innovators, empowering organizations to provide exceptional customer experience through deep understanding of the customer persona.
End-user Adoption:
With an increase in competition, major market players have acquired companies to expand their market penetration and reach. For instance, in April 2020, Accenture acquired Revolutionary Security LLC, to strengthen its product portfolio in cyber security and to provide clients with better protection solutions for data to defend their organizations across their entire ecosystem. Revolutionary Security LLC is a US-based company operating in cybersecurity services including assessment and testing, design and building of security programs. The results help organizations prioritize actions to mitigate cyber risks within their enterprise.
In addition, various companies have expanded their current product portfolio with increased diversification among customers, with further growth in investment across the world and the rise in demand for automated breach and attack simulation. For instance, in February, 2023, SecurityGen, a leading provider of security solutions and services for the telecom industry, announced that it is set to focus on Southeast Asia as its growth strategy for 2023. SecurityGen is transforming 5G cyber-security for mobile operators in Southeast Asia and across the world. This move is driven by the 5G networks and the associated launch of new services for subscribers & business customers in the region. Two large telecom operators in Malaysia, Thailand, and Indonesia already use SecurityGen for their mobile network security.
For instance, in December, 2022, Hive Pro announced that it has added a breach and attack simulation feature to its threat exposure management platform, HivePro Uni5, to meet growing customer expectations. Hive Pro's breach and attack simulation (BAS) solution is designed to work with a customer's asset management and vulnerability management & threat management solutions, providing context and intelligence to customers.
Key Benefits for Stakeholders
The study provides an in-depth analysis of the global automated breach and attack simulation market forecast along with current & future trends to explain the imminent investment pockets.
Information about key drivers, restraints, & opportunities and their impact analysis on global automated breach and attack simulation market trends is provided in the report.
The Porter’s five forces analysis illustrates the potency of the buyers and suppliers operating in the industry.
The Automated breach and attack simulation market analysis from 2022 to 2031 is provided to determine the market potential.
Automated Breach and Attack Simulation Market Report Highlights
| Aspects | Details |
| Market Size By 2031 | USD 5.5 billion |
| Growth Rate | CAGR of 33.6% |
| Forecast period | 2021 - 2031 |
| Report Pages | 426 |
| By Offering |
|
| By Deployment Mode |
|
| By Application |
|
| By End User |
|
| By Region |
|
| Key Market Players | Cymulate., XM Cyber, SafeBreach Inc., FireMon, LLC., Rapid7, Qualys, Inc., AttackIQ., Keysight Technologies, Skybox Security, Inc., Sophos Ltd. |
Analyst Review
Automated breach and attack simulation (ABAS) is a technique for testing and improving the security posture of an organization's network and infrastructure. In addition, ABAS tools automate the process of simulating attacks and breaches to identify vulnerabilities and configuration weaknesses. Moreover, ABAS enables organizations to continuously test their security posture, allowing them to identify weaknesses and prioritize remediation efforts. By simulating attack scenarios, ABAS tools can help organizations understand the impact of an attack and improve their incident response capabilities. They also help organizations stay up-to-date with the latest attack techniques and tactics.
The global automated breach and attack simulation market is expected to register high growth due to increase in security investment and rise in concern over complying with security regulations. Thus, increase in adoption of automated breach and attack simulation, owing to its security is one of the most significant factors driving the growth of the market. Various companies have established alliances to increase their capabilities with surge in demand for automated breach and attack simulation. For instance, in April 2022, AttackIQ partnered with Vectra, an AI-driven threat detection and response platform to detect attacks that have bypassed existing security controls and ensure rapid response to the latest threats.
In addition, with further growth in investment across the world and the rise in demand for automated breach and attack simulation, various companies have expanded their current product portfolio with increased diversification among customers. For instance, in January 2023, SafeBreach launched Threat Intelligence Collective, a collaboration that enables seamless integration between the SafeBreach BAS platform and leading threat intelligence providers and platforms.
Moreover, with increase in competition, major market players have started acquisition companies to expand their market penetration and reach. For instance, in December 2022, ReliaQuest acquired Threatcare to automate threat detection and response. Moreover, it allows customers to quickly see the results of a simulated attack from both the point of view of the attacker and the defender, ensuring superior detection and response across all of their security controls.
The automated breach and attack simulation market is projected to reach $5,486.99 million by 2031.
The automated breach and attack simulation market is estimated to grow at a CAGR of 33.6% from 2022 to 2031.
The key players profiled in the report include AttackIQ, Keysight Technologies, Qualys, Inc., Rapid7, Sophos Ltd., Cymulate, FireMon, LLC., SafeBreach Inc., Skybox Security, Inc, Skybox Security, Inc, and XM Cyber.
Asia-Pacific is expected to witness significant growth during the forecast period
Increase in complexities in managing security threats and surge in demand for prioritizing security investments boost the growth of the global automated breach and attack simulation market. In addition, rise in number of cyber-attacks across the globe is positively impacting the growth of the automated breach and attack simulation market.
Loading Table Of Content...
Loading Research Methodology...


