Table Of Contents
- Current Trends and Future Growth Prospects
- Information Technology (IT) Security as a Service Market in the Last Decade
- Innovative information technology (IT) security as a service solution
- Future of Information Technology (IT) Security as a Service: Opportunities and Challenges
- Technological Advancements
- Growing Incidence of Data Breaches
- High Costs Associated with On-premises Solutions
- A Bright Future for the Industry

Onkar Sumant

Pooja Parvatkar
Information Technology (IT) Security as a Service Market: Market Trends and Analysis

The information technology (IT) security as a service market is a rapidly evolving sector experiencing significant growth and demand globally. This growth is primarily driven by rise in adoption of cloud computing, which has transformed the way businesses manage their security needs. As organizations move their operations to the cloud, they require security solutions that can protect their data and applications from cyber threats. This has led to rise in demand for information technology (IT) security as a service offering, which provide a range of security services, including threat detection, incident response, and compliance management, delivered through a cloud-based model.
Another key driver for the information technology (IT) security as a service market is the evolving cyber threat landscape. Businesses are facing increasingly sophisticated cyber-attacks, such as ransomware and phishing, which require comprehensive security solutions. Information technology (IT) security as a service providers offer advanced security technologies and expertise to help businesses protect against these threats. For instance, in March 2022, HelpSystems announced that it has signed a merger agreement to acquire Alert Logic, a well-known leader in managed detection and response (MDR) services. Alert Logic works as a seamless extension of security teams, augmenting existing cybersecurity resources and technology to safeguard on-premises, cloud, SaaS, and hybrid infrastructures. The Alert Logic’s MDR solution focuses on alleviating the intense pressure organizations face due to the increase in cyberattacks and the notable shortage of skilled professionals available to prevent and remediate them. Alert Logic is expected to become a cornerstone of HelpSystems’ comprehensive cybersecurity portfolio.
Current Trends and Future Growth Prospects
Regulatory compliance is driving the adoption of information technology (IT) security as a service. Stringent regulations, such as GDPR and CCPA, require businesses to implement robust security measures to protect sensitive data. Providers in the market offer solutions that help businesses meet these regulatory requirements, providing peace of mind, ensuring compliance. Key players in the market include Cisco, Symantec (now part of Broadcom), and IBM.
Looking ahead, the information technology (IT) security as a service market is expected to see continued growth and innovation. Advanced threat detection technologies, such as artificial intelligence and machine learning, are expected to play a key role in detecting and responding to cyber threats in real-time. Integration with IoT security is also expected to increase, as the Internet of Things (IoT) continues to grow, and businesses seek to secure IoT devices and networks.
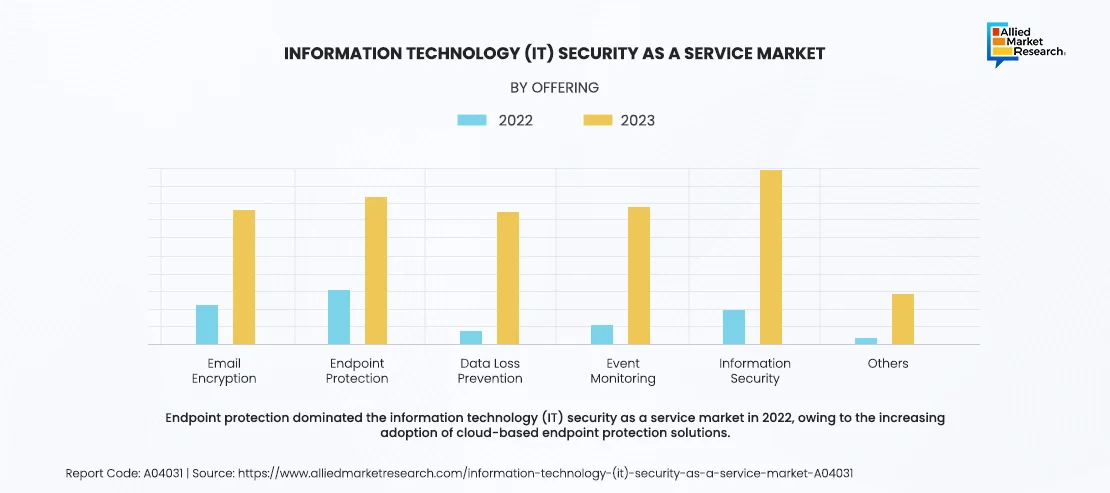
Information Technology (IT) Security as a Service Market in the Last Decade
Over the last decade, there has been a rise in adoption of cloud computing. As businesses move their operations to the cloud, they require security solutions that can protect their data and applications from cyber threats. For instance, in June 2021, Professional networking giant, LinkedIn saw data associated with 700 millions of its users posted on a dark web forum, impacting more than 90% of its user base. Moreover, a scraped data sample posted by the hacker contained information including email addresses, phone numbers, geolocation records, genders, and other social media details, which would give malicious actors plenty of data to craft convincing, follow-on social engineering attacks in the wake of the leak, as warned by the UK’s NCSC. Information technology (IT) security as a service providers have capitalized on this trend by offering cloud-based security solutions that can scale with the needs of businesses. Another factor driving the growth of the information technology (IT) security as a service market has been the evolving cyber threat landscape. Over the last decade, businesses have faced increasingly sophisticated cyber-attacks, such as ransomware and phishing. Information technology (IT) security as a service providers have responded by offering advanced security technologies and expertise to help businesses protect against these threats. Regulatory compliance has also been a key driver for information technology (IT) security as a service market in the last decade. Stringent regulations, such as GDPR and CCPA, require businesses to implement robust security measures to protect sensitive data. Information technology (IT) security as a service providers have offered solutions that help businesses meet these regulatory requirements, providing peace of mind and ensuring compliance.
Innovative information technology (IT) security as a service solution
Advanced Threat Detection: Advanced threat detection solutions leverage technologies such as artificial intelligence and machine learning to identify and respond to sophisticated cyber threats in real-time. These solutions analyze network traffic, user behavior, and system logs to detect anomalies and potential security breaches, allowing organizations to respond quickly and effectively to mitigate risks.
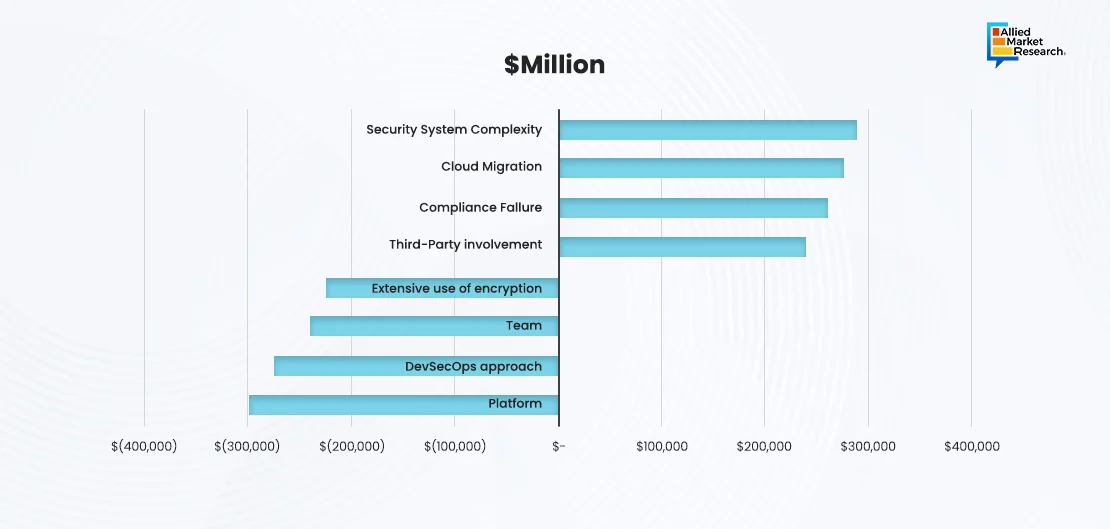
Cloud Security: Cloud security solutions protect data, applications, and infrastructure hosted in the cloud from cyber threats. These solutions include firewalls, encryption, and access control mechanisms to ensure that data is secure and compliant with regulations. Cloud security solutions are essential for businesses adopting cloud computing to protect their digital assets from unauthorized access and cyber-attacks.
Endpoint Protection: Endpoint protection solutions protect endpoints, such as laptops, desktops, and mobile devices, from malware, ransomware, and other cyber threats. These solutions include antivirus software, firewalls, and intrusion detection systems to detect and block malicious activities on endpoints. Endpoint protection solutions are essential for businesses with remote or mobile workers to secure their devices and data from cyber-attacks. In June 2023, Check Point® Software Technologies Ltd., a leading provider of cybersecurity solutions globally, partnered with communications technology company, TELUS, to launch the TELUS Cloud Security Posture Management (CSPM) service in Canada. Backed by Check Point’s AI-powered threat prevention and high-fidelity posture management technology, TELUS CSPM provides a comprehensive managed solution for Canadian organizations to monitor cloud security posture in real-time and detect, remediate, and report on vulnerabilities.
Identity and Access Management (IAM): IAM solutions manage and control access to systems and applications based on user identities. These solutions include multi-factor authentication, single sign-on, and privileged access management to ensure that only authorized users have access to sensitive data and resources. IAM solutions are essential for businesses to protect against unauthorized access and data breaches.
Security Information and Event Management (SIEM): SIEM solutions collect, analyze, and correlate security events and logs from various sources to detect and respond to security incidents. These solutions provide real-time visibility into the organization's security posture, enabling security teams to identify and mitigate threats quickly. SIEM solutions are essential for businesses to monitor and manage their security infrastructure effectively. In September 2023, Check Point Software Technologies Ltd., a global leader in cybersecurity solutions, acquired Atmosec, an innovative Software as a Service (SaaS) security vendor. This acquisition underscores Check Point’s commitment to bolster its SaaS security offerings and address the growing cybersecurity challenges faced by organizations in an increasingly SaaS-driven world.
Future of Information Technology (IT) Security as a Service: Opportunities and Challenges
The information technology (IT) security as a service market has promising growth opportunities, driven by rise in technological advancements and rise in incidences of data breaches. However, high cost of these services is a major restraint for the growth of the market.
Technological Advancements
Information technology (IT) security as a service has witnessed significant technological advancements in recent years, enhancing its capabilities to safeguard organizations against evolving cyber threats. One notable advancement is the integration of artificial intelligence (AI) and machine learning (ML) into security services. These technologies enable advanced threat detection by analyzing vast datasets to identify patterns and anomalies indicative of potential security incidents. Automation has also played a crucial role, allowing for real-time responses to security events and streamlining routine tasks, thus improving overall efficiency. For instance, in January 2024, Kyndryl, the world's largest technology infrastructure services provider, launched two new security edge services developed jointly with Cisco to help customers improve their security controls and proactively address and respond to cyber incidents. The new security edge services, combined with Kyndryl and Cisco's available SD-WAN services, enable enterprises to build a solid foundation to transition into a secure access service edge (SASE) architecture. Kyndryl then delivers these services and solutions to help customers meet their business needs in areas of application modernization, resilient networks and secure infrastructure with zero trust network and hybrid work.
Growing Incidence of Data Breaches
The escalating frequency and severity of data breaches have catalyzed a transformative shift in how organizations approach their cybersecurity strategies, particularly fueling the surge in demand for IT security as a service. The traditional reactive measures are proving inadequate in the face of increasingly sophisticated cyber threats that exploit vulnerabilities in both technology and human factors. High-profile incidents of data breaches have not only led to financial losses but have also eroded the trust of consumers and partners. As a response, businesses are recognizing the limitations of in-house security solutions and are turning to security-as-a-service models that offer continuous monitoring, threat intelligence, and adaptive defenses. For instance, in June 2021, cyber analytics firm Cognyte failed to secure its database, exposing 5 billion records detailing previous data incidents. The records were posted online without a password, or any other authentication required to access them. The database was exposed for four days, and it is not clear precisely how many passwords were included, but all contained names, email addresses, and the data source.
High Costs Associated with On-premises Solutions
Rise in costs associated with on-premise security solutions are compelling organizations to reconsider their cybersecurity strategies and opt for more cost-effective IT security as a service. On-premise solutions traditionally require substantial investments in hardware, software licenses, and skilled personnel for deployment and ongoing maintenance. For instance, according to the 2023 cost of a data breach report by IBM, data breaches in hybrid cloud environments cost $440,000 less than public, private, and on-premise cloud models. However, hybrid cloud environment data breaches cost an average of $3.80 million, compared to $4.24 million in a private cloud environment. As cybersecurity threats become more sophisticated and dynamic, the need for regular updates and enhancements to on-premise systems put a continuous financial strain on organizations. The flexibility and scalability inherent in security-as-a-service models provide a viable solution to these challenges. Cloud-based security services eliminate the need for significant upfront capital investments, offering a subscription-based pricing structure that aligns more closely with operational expenses. This pay-as-you-go model allows organizations to scale their security infrastructure according to their needs, avoiding the financial burden of overprovisioning for potential future threats. In addition, the outsourcing of security functions to specialized service providers in the cloud allows organizations to leverage the provider's expertise and infrastructure, reducing the need for in-house security personnel and further streamlining costs.
A Bright Future for the Industry
In conclusion, the information technology (IT) security as a service market is evolving rapidly, driven by technological advancements, the changing cyber threat landscape, and regulatory requirements. Businesses are increasingly turning to information technology (IT) security as a service providers to help them protect their data and applications from cyber threats. With the continued adoption of cloud computing and the growing complexity of cyber threats, the information technology (IT) security as a service market is expected to continue to grow in the coming years.
For further insights, get in touch with AMR analysts.

